How to Safely Store Cryptocurrency Offline
How to safely store cryptocurrency offline is a crucial aspect of digital asset security. The increasing popularity of cryptocurrencies has unfortunately also led to a rise in theft and hacking incidents. Unlike traditional banking systems, cryptocurrency transactions are irreversible, making secure storage paramount. This guide explores various offline methods, weighing their pros and cons, to help you confidently protect your digital assets.
Protecting your cryptocurrency investments requires a proactive approach to security. This guide will delve into the intricacies of hardware wallets, paper wallets, and seed phrase management, offering a comprehensive understanding of each method’s strengths and vulnerabilities. We will also examine real-world examples and provide practical steps to ensure the long-term safety of your holdings. By the end, you’ll be equipped to make informed decisions about the best offline storage strategy for your specific needs and risk tolerance.
Understanding Offline Cryptocurrency Storage Risks
Securing your cryptocurrency offline significantly reduces the risk of theft compared to online methods. However, understanding the vulnerabilities of online storage and the potential threats associated with it is crucial for appreciating the value of offline solutions. This section details the inherent risks of keeping your digital assets connected to the internet and highlights the superior security offered by offline storage.Online cryptocurrency storage, while offering convenience, exposes your assets to a wide range of threats.
The constant connectivity required for online wallets and exchanges makes them prime targets for malicious actors. These threats range from sophisticated hacking attempts targeting exchanges to simpler phishing scams aimed at individuals.
Vulnerabilities of Online Cryptocurrency Storage
Online storage methods, such as web wallets and exchange platforms, are inherently vulnerable due to their reliance on internet connectivity. This connectivity creates multiple attack vectors. Hackers can exploit vulnerabilities in the platform’s software, use malware to steal login credentials, or employ phishing techniques to trick users into revealing their private keys. Furthermore, exchanges themselves are targets for large-scale hacks, as evidenced by numerous high-profile incidents in the past.
The risk of data breaches and subsequent loss of funds is ever-present. This contrasts sharply with offline storage, where the lack of internet connection eliminates many of these vulnerabilities.
Securing your cryptocurrency offline involves using hardware wallets or paper wallets for enhanced security. Understanding the risks associated with online storage is crucial, and this is particularly relevant when considering how digital assets integrate into broader financial practices within a culture like the American lifestyle , where technological adoption is high. Therefore, prioritizing offline storage methods remains a vital aspect of responsible cryptocurrency ownership.
Potential Threats Associated with Internet Connectivity and Exchange Platforms
Internet connectivity introduces a significant risk factor. Malicious actors can leverage various methods to gain unauthorized access to online wallets or exchanges. This includes sophisticated hacking techniques targeting platform vulnerabilities, distributed denial-of-service (DDoS) attacks to disrupt services, and malware designed to steal login credentials or private keys. Exchange platforms, while offering convenience, are centralized entities that become attractive targets for large-scale attacks.
A successful breach can result in the loss of funds for numerous users. Phishing scams, where users are tricked into revealing sensitive information, also pose a substantial threat. In contrast, offline storage mitigates these risks by eliminating the need for internet connectivity.
Comparison of Online and Offline Storage Security Levels
The security levels differ significantly between online and offline storage. Online storage, characterized by constant internet connectivity, inherently carries a higher risk of theft and loss due to the aforementioned vulnerabilities. Offline storage, on the other hand, significantly reduces this risk by removing the primary attack vector: internet access. While offline storage isn’t entirely immune to risks (e.g., physical theft or loss of the storage device), the probability of loss due to hacking or exchange breaches is dramatically lower.
The comparison can be visualized as a spectrum, with offline storage representing a significantly more secure position.
Real-World Examples of Offline Storage Preventing Cryptocurrency Theft
Numerous instances demonstrate the effectiveness of offline storage in preventing cryptocurrency theft. For example, during the 2014 Mt. Gox exchange hack, users who stored their Bitcoin offline were unaffected. Similarly, during various other exchange breaches, users who held their cryptocurrency in offline wallets were able to retain their assets. These real-world scenarios highlight the crucial role of offline storage in mitigating the risks associated with online exchanges and the vulnerabilities of internet-connected wallets.
These cases underscore the importance of considering offline storage as a critical component of a robust cryptocurrency security strategy.
Hardware Wallets

Source: revolutionmining.io
Hardware wallets offer a significant upgrade in security for offline cryptocurrency storage compared to software wallets or paper wallets. They are physical devices designed to generate and store private keys offline, minimizing the risk of hacking or malware compromising your funds. This enhanced security comes at the cost of slightly higher upfront investment and a less user-friendly experience compared to software solutions.Hardware wallet functionality centers around secure key generation and management.
The device itself generates and stores your private keys, never exposing them to the internet or potentially vulnerable software. Transactions are signed directly on the device, ensuring that even if your computer is compromised, your cryptocurrency remains safe. Most hardware wallets offer additional security features like PIN codes, recovery phrases (seed phrases), and potentially even biometric authentication.
Hardware Wallet Brands and Security Protocols
Several reputable brands dominate the hardware wallet market, each employing distinct security protocols. Ledger and Trezor are two of the most well-known, both employing robust security measures such as tamper-evident designs and secure elements (specialized chips designed to protect cryptographic keys). Coldcard, another popular choice, focuses on open-source software and emphasizes a strong emphasis on security auditing. Each brand’s security protocols vary slightly, but generally involve secure key generation, signing of transactions offline, and protection against physical tampering.
Choosing a reputable brand with a strong track record and community support is crucial.
Hardware Wallet Setup and Usage
Setting up a hardware wallet involves a few crucial steps. First, you’ll need to carefully unpack the device and connect it to a computer. The wallet will guide you through the process of creating a new wallet and generating a unique recovery phrase (seed phrase). This phrase is critically important – it’s your backup and allows you to restore your wallet if the device is lost or damaged.
Securing your cryptocurrency offline involves using hardware wallets or paper wallets for optimal protection. Understanding the risks involved requires a solid grasp of financial literacy, something often emphasized within the US education system , particularly at higher education levels. Therefore, investing time in learning about financial security complements the technical aspects of offline cryptocurrency storage.
Never share this phrase with anyone. After setting up the wallet, you can use the accompanying software to manage your cryptocurrencies. The interface varies by brand but generally involves viewing balances, sending and receiving cryptocurrency, and managing multiple accounts.
Securely Transferring Cryptocurrency to a Hardware Wallet
Transferring cryptocurrency to a hardware wallet is a crucial step in securing your assets. The process is generally straightforward, but it’s essential to follow each step carefully to avoid errors.
- Obtain your hardware wallet’s public address: Your hardware wallet will display a unique public address for each cryptocurrency you wish to store. This is the address you will provide to the sender.
- Verify the address: Double-check that the public address displayed on your hardware wallet matches the address you are providing to the sender. A single typo can result in irreversible loss of funds.
- Initiate the transfer from your exchange or software wallet: Using your exchange or software wallet, initiate a transfer of your cryptocurrency to the public address you’ve obtained from your hardware wallet. Be sure to specify the correct cryptocurrency and network (e.g., Bitcoin, Ethereum, etc.).
- Confirm the transaction: Once the transaction is initiated, it will need to be confirmed on the blockchain. The time required for confirmation varies depending on the cryptocurrency and network congestion.
- Verify the transaction: After sufficient confirmations, verify that the cryptocurrency has been successfully received by your hardware wallet.
Hardware Wallet Comparison
| Hardware Wallet | Price (USD) | Security Features | Supported Cryptocurrencies |
|---|---|---|---|
| Ledger Nano S Plus | $79 | Secure element, PIN code, recovery phrase, firmware updates | Over 5,500 crypto assets |
| Trezor Model One | $59 | Secure element, PIN code, recovery phrase, open-source firmware | Bitcoin, Ethereum, and other major cryptocurrencies |
| Coldcard | $199 | Open-source firmware, advanced security features, large screen | Bitcoin and other cryptocurrencies (support varies by model) |
| KeepKey | $49 | Secure element, large screen, open-source firmware | Bitcoin, Ethereum, Litecoin, Dogecoin and others |
Paper Wallets
Paper wallets offer a simple, offline method for storing cryptocurrency. They involve generating a private and public key pair and printing them onto paper. While seemingly straightforward, creating and securing a paper wallet requires meticulous attention to detail to mitigate significant risks.Paper wallets are essentially a physical representation of your cryptocurrency addresses. The public key, which is like your bank account number, is used to receive funds, while the private key, akin to your bank password, is essential for authorizing transactions.
Losing your private key means losing access to your cryptocurrency.
Paper Wallet Generation and Printing
Generating a paper wallet involves using specialized software or online tools designed for this purpose. These tools create a QR code representing your public and private keys. It is crucial to use a computer that has never been connected to the internet or has been thoroughly sanitized. This prevents any potential malware from intercepting your keys. After generating the keys, print them on high-quality, tamper-evident paper using a printer that is not connected to a network.
Avoid using inkjet printers, as the ink can fade over time. Laser printers offer better longevity and security. Consider using a printer with a built-in shredder for immediate disposal of any failed prints or unused paper.
Offline Device Usage and Secure Printing Methods
The entire process of generating and printing a paper wallet must occur on an offline device. This means a computer that has never been connected to the internet or a network, and is free from any malware or viruses. This offline environment is critical to preventing the interception of your private key. Secure printing methods involve using high-quality, tamper-evident paper, a laser printer, and immediately shredding any failed prints or unused paper.
Consider using a printer that allows for the printing of multiple copies to increase redundancy.
Risks Associated with Paper Wallet Storage and Handling
Paper wallets are vulnerable to a range of threats. Physical damage, such as water damage, fire, or tearing, can render the keys unreadable. Theft is another major concern; a stolen paper wallet grants immediate access to the cryptocurrency. Additionally, improper handling, like accidental exposure to sunlight, can degrade the paper and the ink over time. Even subtle alterations to the printed keys can render them unusable.
The keys must be protected from all environmental and physical threats.
Best Practices for Securing and Protecting Paper Wallets
To mitigate risks, store your paper wallet in a fireproof and waterproof safe. Consider using multiple safes in different locations for enhanced security. Store it away from any easily accessible locations. Laminating the paper wallet can offer additional protection against moisture and damage. Regularly verify the integrity of the paper wallet by comparing the printed keys with a backup copy.
This is best achieved by comparing the keys with a backup that is stored in a separate location. Never keep the backup copy in the same location as the original wallet.
Verifying the Integrity of a Generated Paper Wallet
Before using a paper wallet, verify the integrity of the generated keys. This involves using a separate offline device and a reputable cryptocurrency wallet to scan the QR code and confirm that the public key corresponds to the expected address. Any discrepancies should be immediately investigated. Double-checking the keys manually, comparing them against the original generation record, is a further step to ensure accuracy.
If any errors or inconsistencies are found, discard the wallet immediately and generate a new one.
Seed Phrase Management and Security
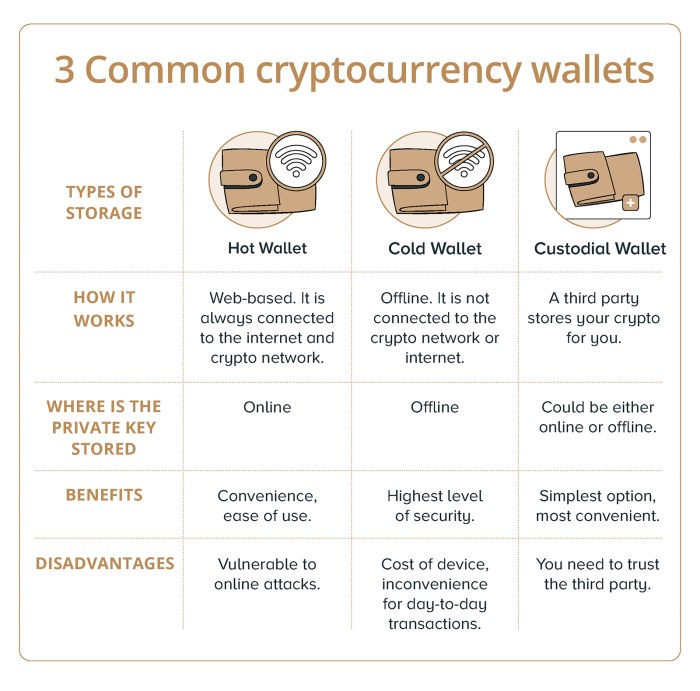
Source: com.sg
Your seed phrase is the bedrock of your cryptocurrency security. It’s a crucial sequence of words that acts as a master key, granting you access to your cryptocurrency holdings across various wallets. Losing or compromising your seed phrase means irreversible loss of access to your funds. Therefore, understanding and implementing robust security measures for its management is paramount.Protecting your seed phrase requires a multi-layered approach, combining physical and procedural safeguards.
Securing your cryptocurrency offline involves using hardware wallets or paper wallets for maximum protection against online threats. For a break from the complexities of digital asset security, you might enjoy exploring what’s predicted for the film industry, such as checking out previews for American movies 2025 , before returning to the crucial task of safeguarding your investments. Remember, proper offline storage is paramount for minimizing the risk of cryptocurrency theft.
The goal is to prevent unauthorized access under any circumstances, including theft, natural disasters, or even accidental destruction. This involves careful consideration of storage location, backup strategies, and overall security protocols.
Securing your cryptocurrency offline involves using hardware wallets or paper wallets, prioritizing robust security measures. For those interested in pursuing careers in cybersecurity, which is crucial for protecting digital assets, consider exploring top programs at institutions like those listed on this helpful resource for USA top universities. Ultimately, understanding the risks and implementing proper offline storage strategies is key to protecting your cryptocurrency investments.
Secure Offline Storage Methods for Seed Phrases
Several methods exist for securing your seed phrase offline. The core principle is to minimize the risk of digital compromise and physical theft. These methods often involve redundancy and diversification to further mitigate risks. A single point of failure, such as relying solely on a single physical location, should be avoided.
Comparing Seed Phrase Safeguarding Strategies
Different strategies offer varying levels of security and convenience. Simply writing it down on paper carries significant risk, while sophisticated methods such as splitting the phrase across multiple locations or using a combination of physical and digital (encrypted) backups provide enhanced protection. The optimal approach depends on individual risk tolerance and the value of the assets involved. For example, splitting the seed phrase into three parts and storing them in separate, secure locations significantly reduces the risk of complete loss compared to keeping the entire phrase in a single place.
Using a hardware encrypted device to store a digital copy offers an additional layer of security compared to a simple handwritten copy.
Examples of Secure Physical Storage Solutions
Secure physical storage solutions should be resistant to fire, water damage, and theft. Examples include:
- Fireproof and waterproof safe: A high-quality safe provides robust protection against common hazards. Consider a safe anchored to the floor or wall for enhanced security against theft.
- Safety deposit box: Banks offer safety deposit boxes, which provide a secure offsite location for storing sensitive documents. However, remember that the bank itself might be vulnerable to natural disasters or security breaches.
- Splitting the seed phrase and storing in geographically diverse locations: This distributes the risk. One part could be stored in a safe at home, another with a trusted family member in a different location, and the third in a safety deposit box.
- Metal plate engraved with the seed phrase: A durable and discreet option. However, ensure the plate is stored securely and protected from damage.
Best Practices for Seed Phrase Management and Protection
Effective seed phrase management necessitates a proactive and diligent approach. The following best practices should be meticulously followed:
- Never share your seed phrase with anyone: This includes family, friends, or even cryptocurrency support teams. Legitimate organizations will never ask for your seed phrase.
- Verify the authenticity of any software or website before entering your seed phrase: Phishing attacks are common. Always double-check URLs and website security certificates.
- Regularly back up your seed phrase using multiple methods: This ensures redundancy in case one method fails.
- Store your seed phrase in a location where it will not be easily discovered: Avoid obvious hiding places.
- Memorize your seed phrase, if possible, and verify it against your written copies periodically: This provides an additional layer of security, but be aware of the risks of memorization errors.
- Use a password manager for any digital copies of your seed phrase: Ensure the password manager itself is highly secure.
- Consider using a hardware security module (HSM) for extremely high-value assets: HSMs provide a highly secure environment for managing cryptographic keys, including seed phrases.
Cold Storage Security Best Practices
Safeguarding your offline cryptocurrency requires a multi-layered approach to security. While hardware and paper wallets offer significant protection against online threats, physical security and diligent management remain crucial for maintaining the integrity of your assets. This section details best practices to mitigate risks and ensure the long-term safety of your cold storage.
Potential Security Threats Associated with Cold Storage
Cold storage, while significantly more secure than online wallets, is not impervious to threats. Physical theft, damage from fire or natural disasters, and even sophisticated social engineering attacks remain potential vulnerabilities. For example, a burglar gaining access to your home could steal your hardware wallet, and a cleverly crafted phishing email could trick you into revealing your seed phrase.
Understanding these threats allows for the implementation of robust preventative measures.
Securing the Physical Environment for Cold Storage
The physical location where you store your cold storage devices significantly impacts their security. Ideally, your cold storage should be kept in a secure, fireproof, and climate-controlled environment, separate from your primary residence if possible. Using a safety deposit box in a reputable bank offers an added layer of protection against theft and fire. Implementing robust security measures at home, such as strong locks, security systems, and discreet storage locations, is also advisable.
Remember, the goal is to make the theft or unauthorized access to your cold storage as difficult and time-consuming as possible.
The Importance of Regular Backups and Verification
Regularly backing up and verifying your cold storage is paramount. This involves creating multiple backups of your seed phrase using different methods (e.g., writing it down on multiple pieces of paper, using a metal plate, splitting it across multiple secure locations). Periodically verifying your seed phrase against your existing backups ensures its accuracy and helps detect any potential errors or corruption.
This process should be treated with the utmost caution, as any mistakes could lead to irreversible loss of funds. Consider using a checksum or hash function to verify the integrity of your backup.
Multi-Signature Wallets and Their Impact on Security
Multi-signature wallets enhance security by requiring multiple parties to authorize transactions. This adds a layer of protection against unauthorized access, even if one key is compromised. For example, a 2-of-3 multi-signature wallet requires two out of three private keys to authorize a transaction, making it significantly more difficult for a thief to spend your funds even if they obtain one key.
The increased complexity of transactions adds a layer of deterrence.
Steps to Take in Case of a Physical Security Breach
In the unfortunate event of a physical security breach involving your cold storage, immediate and decisive action is crucial.
- Report the incident to the appropriate authorities: Contact your local law enforcement immediately to file a police report. This will be crucial for any potential insurance claims or investigations.
- Secure any remaining assets: If you have other cold storage devices or backups, take immediate steps to secure them and relocate them to a safe location.
- Contact your cryptocurrency exchange or wallet provider: Notify them of the breach and take steps to secure any associated accounts. This might involve freezing accounts or changing passwords.
- Monitor your accounts: Regularly check your accounts for any unauthorized activity and take appropriate action if any suspicious transactions are detected.
- Consider professional help: Seek advice from cybersecurity experts or financial advisors to help you navigate the complexities of the situation and mitigate potential losses.
Choosing the Right Offline Storage Method

Source: offtgrid.com
Selecting the optimal offline storage method for your cryptocurrency hinges on a careful evaluation of your individual needs and risk tolerance. The primary choices are hardware wallets and paper wallets, each offering distinct advantages and disadvantages. Understanding these differences is crucial for making an informed decision that protects your digital assets.Hardware wallets and paper wallets represent two fundamentally different approaches to offline cryptocurrency storage.
Both offer strong security against online threats, but their ease of use, cost, and overall security differ significantly.
Hardware Wallet versus Paper Wallet: A Comparison
Hardware wallets, such as Ledger and Trezor devices, are physical devices designed specifically for storing cryptographic keys. They offer a high level of security due to their secure element chips, which protect private keys from external access, even if the device is compromised. However, they come at a higher cost than paper wallets and require a degree of technical proficiency to set up and use.
Loss or damage to the device can result in the loss of funds if a recovery seed phrase is not properly managed.Paper wallets, on the other hand, involve printing your public and private keys onto paper. They are inexpensive and easy to create, but they are significantly more vulnerable to physical damage, theft, or loss. The security of a paper wallet relies entirely on the physical security of the paper itself and the secrecy of the information it contains.
A misplaced or damaged paper wallet could mean irreversible loss of funds.
Factors Influencing Offline Storage Method Selection
Several factors should guide your choice between hardware and paper wallets, or even a combination of both. The amount of cryptocurrency you hold directly impacts your risk tolerance. Holding a large sum necessitates a higher level of security, typically favoring a hardware wallet. Conversely, smaller amounts might justify the simpler, though less secure, approach of a paper wallet.Your technical expertise also plays a crucial role.
Securing your cryptocurrency offline involves using hardware wallets or paper wallets, prioritizing robust security measures. Understanding the financial landscape is crucial, and exploring sectors like those detailed in the overview of Top industries in the USA can help contextualize the broader economic implications of cryptocurrency adoption. Ultimately, responsible offline storage protects your digital assets and contributes to a more secure financial future.
Hardware wallets, while generally user-friendly, require some technical understanding for setup and management. Paper wallets are simpler to create, but even their creation requires careful attention to detail to avoid errors that could compromise security.
Decision-Making Framework for Offline Storage
A simple framework can guide your decision:
- Assess your cryptocurrency holdings: Determine the value of your digital assets. Higher values necessitate stronger security measures.
- Evaluate your technical skills: Honestly assess your comfort level with technology and cryptography. If you lack technical expertise, a simpler solution, perhaps with the assistance of a knowledgeable friend or professional, may be preferable.
- Consider your risk tolerance: How much risk are you willing to accept? Higher risk tolerance might lead to choosing a paper wallet for its simplicity, while lower risk tolerance would favor the enhanced security of a hardware wallet.
- Choose the appropriate method: Based on the above assessment, select the storage method that best aligns with your needs and risk profile. For substantial holdings and lower risk tolerance, a hardware wallet is generally recommended. For smaller holdings and higher risk tolerance, a paper wallet might suffice, provided meticulous security practices are followed.
Assessing Personal Risk Tolerance and Selecting a Suitable Storage Method, How to safely store cryptocurrency offline
Risk tolerance is subjective and depends on your individual circumstances and financial situation. Someone with a high net worth might be more inclined to use a hardware wallet for its enhanced security, even if it’s more complex to use. Conversely, someone with a smaller amount of cryptocurrency might accept a higher level of risk and opt for a paper wallet, understanding the potential downsides.For example, an individual holding a significant portion of their savings in Bitcoin might choose a hardware wallet and potentially even utilize a multi-signature setup for added security.
In contrast, someone holding a small amount of cryptocurrency for experimentation might feel comfortable using a paper wallet, acknowledging the higher risk of loss. The key is to make an informed decision based on a realistic assessment of your own risk tolerance and the value of your holdings.
Concluding Remarks
Securing your cryptocurrency offline requires careful consideration and a multi-layered approach. While hardware wallets offer robust security features, paper wallets provide a simpler, albeit riskier, alternative. Regardless of your chosen method, diligent seed phrase management is absolutely critical. Remember, the ultimate goal is to minimize your exposure to online threats and protect your investment through a combination of secure hardware, meticulous planning, and a clear understanding of the inherent risks.
By implementing the strategies Artikeld in this guide, you can significantly reduce the likelihood of loss and maintain control over your digital assets.
Question Bank: How To Safely Store Cryptocurrency Offline
What is a seed phrase, and why is it so important?
A seed phrase is a series of words that acts as a key to access your cryptocurrency. It’s essential because it allows you to recover your funds if your hardware wallet is lost or damaged. Protecting your seed phrase is paramount to securing your investment.
Are there any risks associated with using a hardware wallet?
While hardware wallets are significantly more secure than online exchanges, they are not entirely risk-free. Potential risks include physical theft, device malfunction, and the possibility of sophisticated attacks targeting firmware vulnerabilities. It’s crucial to select a reputable brand and follow best security practices.
How often should I back up my cold storage?
Regular backups are crucial. The frequency depends on your risk tolerance and the value of your holdings. At a minimum, annual backups are recommended, but more frequent backups (e.g., semi-annually) are advisable for larger holdings.
What should I do if my hardware wallet is lost or stolen?
Immediately secure your seed phrase if you have not already done so. Contact your hardware wallet provider for support. If you have multiple backups of your seed phrase, follow your pre-determined recovery plan.
Can I use a paper wallet for large amounts of cryptocurrency?
While possible, using a paper wallet for significant amounts of cryptocurrency is generally discouraged due to the increased risk of loss or theft. Hardware wallets offer superior security for substantial holdings.